Top Considerations for Utility Cybersecurity in the Water Industry
About the author:
David Trepp is partner and part of the information security assessment team for BPM. Trepp can be reached at [email protected].
Providing an adequate level of IT security for water and wastewater utility industry leaders has become a high-profile challenge, as organizations of all sizes find themselves on the front lines of the global ransomware war. Additionally, in a pandemic telework environment, many agencies find their attack surface area increased, as administrative users that previously had their workstations safely ensconced behind corporate firewalls are now sharing home Wi-Fi with family members behind a telco modem. To further compound the challenge, the water and wastewater utility industry is faced with increasingly distributed IT systems, as cloud infrastructure, hosted applications, and outsourced services blur the boundaries between industrial controls systems (and protected customer/employee data) and the rest of the world.
In this article, we will bring an attacker’s perspective to defining the issues and discussing actionable steps all water and wastewater utility industry leaders can oversee to provide effective IT assurance activities that will help keep your company or utility from becoming the next victim.
Primary Cybersercurity Threat Sources & Scenarios
At the highest level, we can distinguish four main populations of threat sources: nation-state sponsored entities, cyber criminals, hacktivists and insiders. The first two groups, nation-state entities and cybercriminal gangs, are of particular concern for water and wastewater utilities.
The first group of threat sources are foreign nation-state sponsored hacking groups, e.g. China, North Korea, Russia, Iran, etc. These groups may be seeking proprietary intellectual property or preparing for attacks on the availability of key infrastructure components. For infrastructure attacks, the goal is to interrupt service, preferably on a wide scale. These efforts range from performing reconnaissance for unpatched or insecurely configured systems, to actively attempting to place time bombs on these hosts.
Cybercriminals are groups seeking profit from cyberattacks. The most popular form of for-profit attacks in 2020 is ransomware, where the attacker encrypts the victim organization’s data and extorts a ransom for the decryption key that will allow the organization to resume operations. Other techniques include stealing Personally Identifiable Information (PII) for sale on the dark web, attacking credit card transactions, accounts payable fraud and simple forms of data ransom, where sensitive information is stolen and ransomed back to the owner.
At this point, the reader may be thinking my little water or wastewater system is not of interest to any of these threat populations. This thinking was probably accurate as of just a few years ago. However, today, organizations of absolutely all sizes are targeted by these groups. As long as your organization has two Bitcoins to rub together, any cybercriminal will take any amount of ransom money. The key to foreign nation-state sponsored groups’s goal of current or future attacks against our nation’s infrastructure will only be effective if a critical mass of systems can be simultaneously interrupted. Security by obscurity is no longer a viable defense strategy.
The final two threat populations pose less likelihood of direct attack to utilities are hackivists, those seeking some form of digital vigilante justice, and malicious insiders, whether employees, contractors or members of the janitorial staff, who have facility access. While less likely to target water and wastewater organizations, these two threat sources cannot be ignored.
Inventory Assets & Data
At the strategic level, the first thing all organizations should do is rigorously inventory data assets and data stores. Know where your data are stored and transmitted. Define who has system and data ownership responsibility and who is responsible for securing the data and key systems, e.g. SCADA. Only by knowing exactly what data and systems your organization manages, and how you transmit and store it, can you begin to provide assurance about its confidentiality, integrity and availability (CIA).
Manage Vendors
Next, make sure you have strong contractual arrangements with your key vendors, service providers and partners. Whether your relationship is with a cloud application vendor or a key underwriter, strong interconnect security agreements provide the foundation for assurance across boundaries. From data classifications to rules of behavior and incident reporting, a strong agreement defines responsibilities and reduces ambiguity. For clear guidance on what is essential to include in interconnect agreements, see the National Institute of Standards and Technology Special Publication 800-47 Security Guide for Interconnecting Information Technology Systems at bit.ly/interconnectstandards.
Transfer Risk via Insurance
We are often asked about cyber liability insurance and related products. Our typical answer is that in our current multi-party liability landscape, the devil is in the policy details. Whether selling or buying, all parties should make themselves well-aware of policy terms. An easy example is defining exactly what systems, applications and data sets are covered by the policy, e.g. are industrial controls systems covered? How about mobile devices? Or cloud applications and systems? The web of interconnected systems makes it difficult for underwriters to cover everything and difficult to afford for policy holders, if the policy is all-inclusive. It is also important to know exceptions in coverage based on inadequate due diligence, e.g. what if the policy holder is not adequately performing configuration management (missing patches) or adequate vendor management (including vendors in tests or collecting evidence of their due diligence activities)? All parties must also agree on what, exactly, constitutes a covered breach, e.g. is a physical theft of information assets a covered act? How about coverage of a state-sponsored attack? Is an inadvertent disclosure of PII covered? The list goes on.
Deploy & Manage Proactive Technical Security Controls
The technical controls we find most effective at thwarting attacks are preventative controls that reduce the likelihood of a successful attack and compensating controls, which limit the impact should a breach occur. While by no means comprehensive, here is a list of a few technical controls that often stymie our penetration test attacks: inbound email and 0365 configuration controls, intrusion detection and prevention systems, rogue host prevention/network access controls, promiscuous protocol, e.g. LLMNR, NBT-NS, MDNS, etc. prohibitions and egress controls.
Test, Test, Test & Test Again
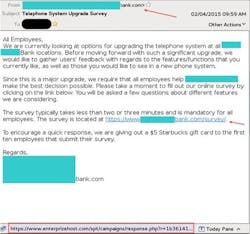
We must “trust but verify.” Only penetration testing of controls can validate weaknesses in IT defenses. Testing must be comprehensive, across not only technical controls but also human and physical safeguards. A simple human attack, in the form of a phishing email, can lead to a massive breach. On page 8 is an example of a modern phish email with some hallmarks of phish attacks listed on the right.
Testing technical controls alone will not answer the question, “How can hackers successfully attack my IT systems?” Comprehensive testing, including an array of technical, human and physical tests, will reveal cascading sequences of exploits that may lead from zero to control of your system in a way vulnerability scans or documentation reviews can never achieve.
Telework Security Controls
As utility system administrators are faced with new telework security challenges, below are five pieces of advice on remote work security controls. As above, these have been prioritized based on what is easiest for attackers to exploit.
1. Establish Robust Telework Security Controls
Users, who had previously been safely ensconced behind the corporate firewall, may now be working from a home network protected from the internet by an ISP modem. However, the firewall is only one element in a robust endpoint security posture. Other key (endpoint) security controls that water and wastewater organizations will want to implement include antivirus and anti-malware software, strong browser controls and a virtual private network (VPN) encrypting all traffic. Together, these controls limit the amount of damage any user can do even if they let their guard down.
2. Encrypt Employee Hard Drives
Also, with so many employees still working remotely all or part of the time, there is an increased risk of sensitive data falling into nefarious hands via theft of work devices. The number one thing IT departments can do to avoid device theft from becoming a breach is to encrypt the hard drives of work-issued laptops or other mobile devices, and insist users turn off those devices when not in use. Encrypting the hard drive of each and every employee device ensures that even if criminals gain access to the computer, they are unable to access any sensitive data that might be contained on that device.
3. Leverage Two-Factor Authentication (2FA)
Another issue that arises in work-from-home arrangements is authenticating users, i.e., confirming users are who they say they are. In an office setting, IT at least has the advantage of physical security to deter criminals from gaining access to work devices. However, when log-ins to cloud software and mobile devices are coming in remotely, IT has no way of truly knowing who is trying to access a service or application. In the post-COVID-19 telework environment, a single password is insufficient to confirm user identity. This is where one-time access codes sent to the user’s mobile device or fob can make a huge difference. Studies show that requiring second factors like these make it exponentially more difficult for hackers to gain access to employee accounts. The good news is that most software and services already have 2FA features built in; all IT needs to do is enable and administer them.
4. Enable Video Call Security Features
Video calls are the area of telework that has garnered the most attention in terms of cybersecurity. While criminals gaining access to Zoom meetings and the like is still a relatively rare occurrence, the worry on the part of users and IT teams is real. That is why utility organizations must be vigilant about enforcing universal use of available security features like unique meeting IDs and meeting passwords. Even better than that is configuring your video communications tool to mandate usage of these features by default. In short, IT organizations should take the time to review and audit the security features of the telework platforms to confirm that they are providing maximal security.
5. Mandate WPA2 (or Better) for Home WiFi
When employees work from home, their home wireless network can become a key point of weakness in your organization’s security posture. The issue is that many individuals use the default router given to them by their ISP, which may or may not have proper security controls installed, or are using older routers. Many older routers use WEP or WPA1 encryption, which make use of notoriously weak algorithms, to secure access. It should go without saying that WEP and WPA1 are unacceptable risks, when all hackers need to do to steal data is drive around looking for weak WiFi networks. The minimum standard for WiFi network security in 2020 is WPA2. To ensure that weak WiFi networks are not putting a hole in your organization’s whole cybersecurity apparatus, utility organizations might consider having proper WiFi security enabled a condition of working from home. In any case, IT staff should be willing to take the time to work with employees working from home to help them enable strong security at home.
Summary
In closing, providing effective security controls across the boundaries of myriad interconnected systems and teleworkers is a daunting challenge. The terrifying threat landscape we face puts utility and personal interests, if not our very democratic institutions, at stake. The fact that the security of any single entity affects the security of the entire integrated ecosystem demands that we act both individually to secure our own utility systems, as well as in concert with vendors, partners and customers to defend our information systems.